Download Free Vmware Esxi 51 License Key Crack
Attention, Internet Explorer User Announcement: VMware Communities has discontinued support for Internet Explorer 7 and below. In order to provide the best platform for continued innovation, VMware Communities no longer supports Internet Explorer 7. VMware Communities will not function with this version of Internet Explorer. Please consider upgrading to Internet Explorer 8, 9, or 10, or trying another browser such as Firefox, Safari, or Google Chrome.
(Please remember to honor your company's IT policies before installing new software!) • • • •.
Posted on 25 July, 2012 by Kyle Gleed, Sr. Technical Marketing Architect, VMware I came across this question today: “How do I setup password free SSH access to my ESXi hosts”.
Activate with your free esxi license key from. Free ESXi 6.5 - How to Download and get License Keys. Attention, Internet Explorer User Announcement: VMware Communities has discontinued support for Internet Explorer 7 and below. Descargar internet download manager con keygen gratis Air Force veteran Steve. Peachtree 2009 serial.
A quick Google search turned up a lot of good info on this topic, but I didn’t find anything on the vSphere blog so I wanted to chime with a quick post, and hopefully add to what’s already out there. When people ask “how” to enable password free SSH, the question I always ask in return is “should' you enable password free SSH?
In most situations I would dare say the answer is probably not. I often find that the decision to enable password free access is not based on any real requirement, but rather is done for the sake of convenience – admins want easy access to their vSphere hosts. In my opinion, this is a case where security should trump convenience. However, having said that I do realize that there are valid situations where SSH access is unavoidable, and depending the situation it might make sense to enable password free access.
My point here is that just because you can setup password free SSH doesn’t mean it’s a good idea. Keep in mind, once you enable password free SSH: • Anybody with access to the root account on the remote host will have full root access to your ESXi host. Chubold my clone zones. • Root users allowed password free access to ESXi are not affected by password changes. • Root users allowed password free access to ESXi are not affected by lockdown mode. With that I’ll jump down off my soapbox and go over the steps to enable password free SSH. It’s really pretty easy. Two basic steps: 1.
L2 Community Board High Five add Skype Cerenus.1. Board of Directors. High Five Access Media is governed by a group of community volunteers. The towns of Vail, Avon and Minturn appoint one member each to the board of directors. The remaining directors are elected by HFAM members. The Board of Directors typically meets once every quarter at the HFAM center. Community Board 7 only has an advisory vote when it comes to the land-use review phase of Riverside Center, but that hasn't stopped the group from laying down the law and telling developer Extell. Community board high five. Hello ppl.Im selling a special community board with alot usefull features for every low/mid/high rate servers. This community board works on l2j h5 stable version.
On the remote host use “ ssh-keygen” to create a private/public key pair. You can use an RSA or DSA token. Make sure you leave the passphrase empty/blank.
Next, append the user’s public key (created by the ssh-keygen tool) to the /etc/ssh/keys-root/authorized_keys file on the ESXi host. Here’s an easy way to do this (I got this nifty syntax from ): # cat /root/.ssh/id.dsa.pub ssh root@ ‘cat >> /etc/ssh/keys-root/authorized_keys’ With the remote host’s public key stored in the ' authorized_keys' file, anytime this user SSH's to the vSphere host instead of prompting for a password the host will check the remote users public key against what's in the authorized_keys file, and if a match is found access is allowed. Note: I've seen a few articles that mentioned the need to edit the /etc/ssh/sshd_config file. On ESXi 5.0 you do not need to edit the sshd_config file.
The file is already configured to allow password free SSH. All you need to do is load the user's public keys into the /etc/ssh/keys/authorized_keys file. Follow me on twitter @VMwareESXi. August 8th, 2012 Thanks for the mention Kyle, but I can’t take credit for the “nifty syntax”, I found it somewhere long time ago while looking for a fast and reliable way to copy public key to remote host. I also agree with Ed’s comment – it’s best to use password-less logins for automation purposes and definitely not with superuser account.
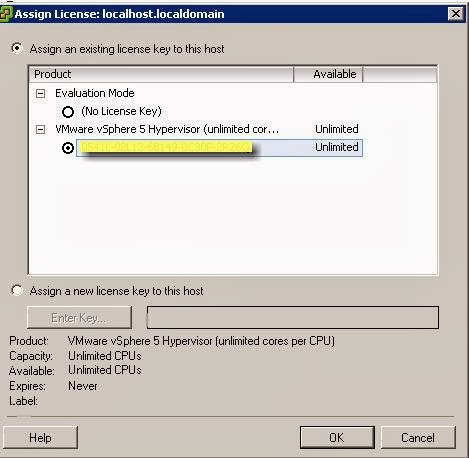
For fast, yet secure login better use ssh-agent or Pagent (on Windows). I made a post on how to streamline this process on Windows by making Pageant automatically load keys on startup: •. December 26th, 2012 According to Kyle Gleed’s instruction, I can enable password free ssh access on ESXi5.1, but can’t for non-root.
I follow steps below trying to enable non-root ssh access on ESXi5.1 and persist my configuration – Use “ssh-keygen” to create a private/public key pair for non-root user – Copy non-root user public key to host at persistent datastore at /vmfs/volumes/datastore1/keys-non-root/authorized_keys – Add these lines to the /etc/rc.local file (for ESXi 5.0) and /etc/profile.local file (for ESXi 5.1): cp -R /vmfs/volumes/datastore1/myStore/keys-oneadmin /etc/ssh I am sure public key for non-root is persistent over reboot the host. But I can’t passwordless access on ESXi host. Anyone has experienced that situation please take time give me your advice.